Disclaimer: edgeminer.org is expiring soon. Please visit http://yinzhicao.org/EdgeMiner/ for updated information. Thanks!
EdgeMiner: Automatically Detecting Implicit Control Flow Transitions through the Android Framework
Overview
A wealth of recent research proposes static data flow analysis for the security
analysis of Android applications. One of the building blocks that these
analysis systems rely upon is the computation of a precise control flow graph.
The callback mechanism provided and orchestrated by the Android framework makes
the correct generation of the control flow graph a challenging endeavor. From
the analysis' point of view, the invocation of a callback is an implicit
control flow transition facilitated by the framework.
Existing static analysis tools model callbacks either through manually-curated
lists or ad-hoc heuristics. This work demonstrates that both approaches are
insufficient, and allow malicious applications to evade detection by
state-of-the-art analysis systems.
To address the challenge of implicit control flow transitions (i.e., callbacks)
through the Android framework, we are the first to propose, implement, and
evaluate a systematic treatment of this aspect. Our implementation, called
EdgeMiner, statically analyzes the entire Android framework to automatically
generate API summaries that describe implicit control flow transitions through
the Android framework. We use EdgeMiner to analyze three major versions of the
Android framework. EdgeMiner identified 19,647 callbacks in Android 4.2,
suggesting that a manual treatment of this challenge is likely infeasible. Our
evaluation demonstrates that the current insufficient treatment of callbacks in
state-of-the-art analysis tools results in unnecessary imprecision.
Motivating Examples
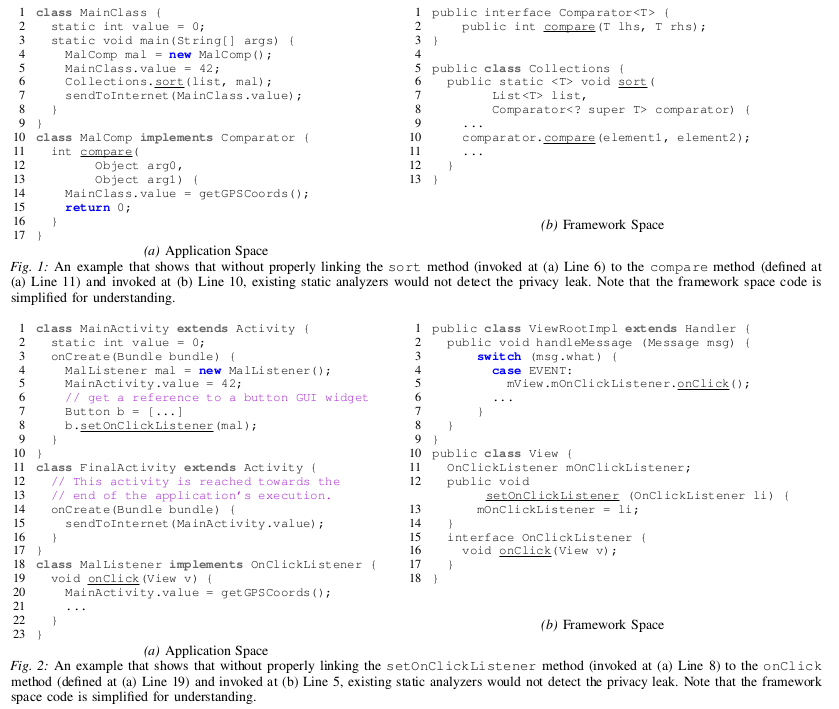
In our research paper, we show how imprecisions related to the missing handling of callbacks through the Android framework can lead to false negatives when performing taint analysis. Figure 1 and 2 report two examples that show how a static analyzer that does not properly handle implicit control flows transitions through the framework would miss to detect privacy leaks.
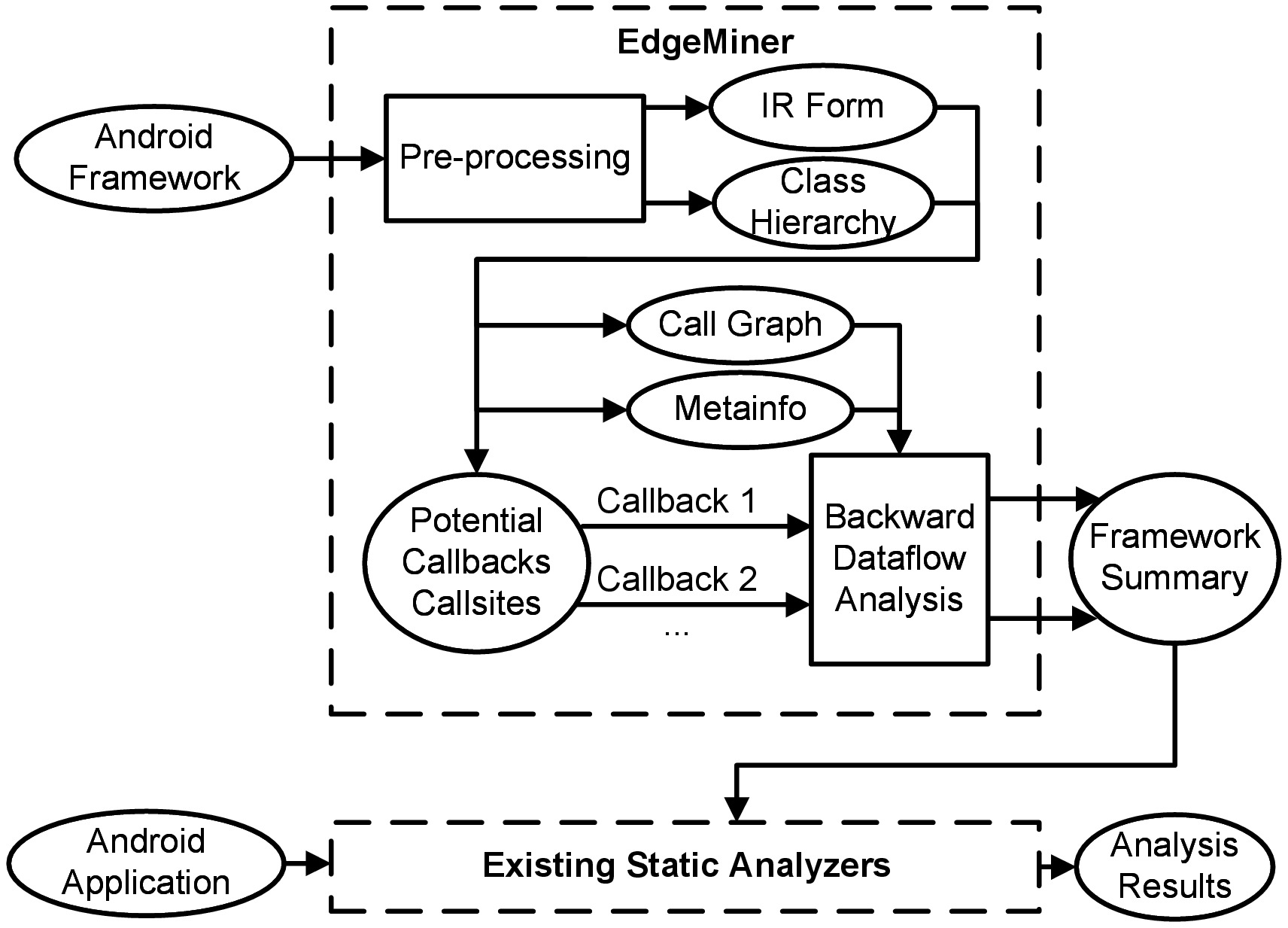
Architecture
Research Paper
EdgeMiner: Automatically Detecting Implicit Control Flow Transitions through
the Android Framework
Yinzhi Cao,
Yanick Fratantonio,
Antonio Bianchi,
Manuel Egele,
Christopher Kruegel,
Giovanni Vigna,
Yan Chen
Proceedings of the Network and Distributed System Security Symposium (NDSS),
San Diego, CA, February 2015.
[PDF] [BibTex]
Dataset Release
We are happy to publicly release the source code of our analyzer, and the full list of implicit edges EdgeMiner extracted for Android 4.2. These results are accessible at this link. These results come in form of a configuration file, and can be easily integrated with existing static analyzers. Feedback and suggestions are very welcome. If you use our dataset, please cite our paper!